CMMC stands for Cybersecurity Maturity Model Certification. This is an initiative of the Department of Defense (DOD) to address cybersecurity concerns at non-governmental organizations participating in the DOD supply chain. The primary goal of CMMC is to improve the protection of sensitive government information and to enhance the reliability of the supply chain. CMMC is based on National Institute of Standards and Technology (NIST) standards SP 800-171, SP 800-172, and a variety of supplemental DOD purchasing clauses (DFARs). CMMC is being implemented in phases over the next three to four years.
CMMC not only applies to DOD prime contractors, but those contractors must pass along the CMMC requirements to all sub-contractors – all the way down the chain until you reach suppliers of COTS products (commercial-off-the shelf products). Essentially, CMMC can apply to anyone producing products designed for, or customized for, a DOD project.
Today, CMMC applies only to DOD projects. However, other federal government agencies are evaluating adoption of CMMC as part of their purchasing processes. With all the supply chain issues industry is facing today and the major disruptions we have seen due to cyberattacks, it is not unreasonable to expect that CMMC, or requirements similar to CMMC, begin to be imposed by any number of commercial companies. Security of the supply chain and protection of sensitive corporate information is an ever-increasing concern for most companies. So even if you are not a supplier to the federal government, you can expect CMMC-like requirements becoming part of your purchasing agreements with your major customers.
What is really involved with CMMC?
Achieving CMMC compliance is a lot more involved than simply adding new security functions to your business’s network – it also involves implementing a series of specific cultural behaviors, policies, and practices within your business. For companies who have sought ISO 9000 compliance, you will recognize that CMMC compliance requires many of the same types of business practices and policies as are required for ISO compliance.
Released November 2021, CMMC 2.0 has streamlined some of the original requirements for CMMC and is currently going through the adoption process. Until fully adopted, the original CMMC requirements are suspended, and CMMC requirements will not be included in DOD purchasing contracts until adoption is complete.
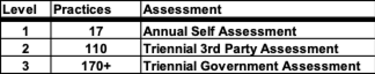
Once adoption of CMMC 2.0 is complete, contracts stipulating CMMC compliance will specify one of three levels of compliance that suppliers must achieve, with each level requiring increasing levels of functionality. The NIST standards define an extensive list of specific practices to be addressed to enhance a business’s security environment. Each level of compliance requires adherence with subsets of these business practices. CMMC also includes assessments to ensure compliance with security standards.
The requirements for compliance at each level are summarized below:

The list of practices is too numerous to list here. You can access the NIST standards at Protecting Controlled Unclassified Information in Nonfederal Systems (nist.gov) (SP 800-171) and Enhanced Security Requirements for Protecting Controlled Unclassified Information: A Supplement to NIST Special Publication 800-171 (SP 800-172). SP 800-171 lists specific practices for addressing a business’s security environment. SP 800-172 defines actions that can be taken to address each of the practices, but does not specify specific tools, products, or architectures required to implement the practices.
Generally, the practices outlined by the NIST standards address the following:
Define and document the practices and procedures you plan to implement to achieve a secure environment.
Train your personnel on these practices and procedures
Implement
Monitor systems and personnel for compliance with your practices and procedures
Document occurrences of non-compliance and implement correct action plans
The practices and procedures defined for CMMC compliance provide well-structured guidance for any company choosing to enhance their security environment. These standards highlight the fact that achieving enhanced security extends well beyond your network technology – incorporating the practices and procedures to be followed by your personnel. In future articles, we will dig deeper into these policies and procedures and explore best practices to achieve an enhanced cybersecurity environment.




